Zero Trust: A Comprehensive Approach to Modern Cybersecurity
In today’s rapidly evolving digital landscape, cybersecurity is a growing concern for businesses, governments, and individuals. With the rise of cloud computing, remote work, and increasingly sophisticated cyberattacks, traditional perimeter-based security models are no longer sufficient to protect sensitive data and systems. This is where Zero Trust comes into play. Zero Trust is a modern cybersecurity framework that assumes no user, device, or network is inherently trusted, regardless of its location inside or outside the organization’s perimeter.
This article will explore Zero Trust, how it works, and the benefits of adopting this security approach.
What is Zero Trust?
Zero Trust is a security concept and framework that operates on the principle of “never trust, always verify.” Unlike traditional security models that rely on a trusted internal network and focus on defending the perimeter (i.e., the network boundary between internal systems and external threats), Zero Trust assumes that internal and external environments are equally vulnerable to attack.
In a zero-trust architecture, every user, device, and network request must be continuously authenticated, authorized, and monitored, regardless of whether the entity is inside or outside the corporate firewall.
Zero Trust aims to minimize the risk of unauthorized access, data breaches, and lateral movement within a network by applying strict access controls and continuously verifying trustworthiness throughout an entity’s interactions with the system.
Core Principles of Zero Trust
There are several principles of zero trust that you need to know, include :
- Verify Identity and Trust at All Times
The fundamental principle of Zero Trust is that Trust should not be automatically granted based on a user or device’s location or network position. Instead, every access request must be verified, regardless of whether the entity is inside or outside the organization’s network.
This involves validating the user’s or device’s identity and ensuring they have the appropriate permissions for the requested action. - Least Privilege Access
In a zero-trust environment, users and devices are granted only the minimum level of access required to perform their tasks. This principle, known as least privilege, limits the exposure of sensitive data and reduces the potential impact of a breach. By granting access only on a need-to-know basis, the attack surface is minimized, and the risk of unauthorized access is significantly reduced. - Micro-Segmentation
Zero Trust involves breaking down the network into smaller, isolated segments, each with its security controls and policies. This practice, known as micro-segmentation, ensures that even if attackers gain access to one part of the network, they cannot move laterally to other parts of the system. Each segment is protected with individual access policies, and only authorized users or devices can access specific resources within each segment. - Continuous Monitoring and Evaluation
Zero Trust requires constant monitoring of user behavior, device health, and network traffic to detect anomalies or suspicious activity. It’s not enough to authenticate and authorize a user at the point of entry; Zero Trust requires continuous validation of Trust throughout the session. Real-time analytics, behavior-based risk assessment, and adaptive access controls are necessary to ensure ongoing security.
Read more Other Articles : Vulnerability Assessment & Penetration Testing: A Comprehensive Guide
How Zero Trust Works
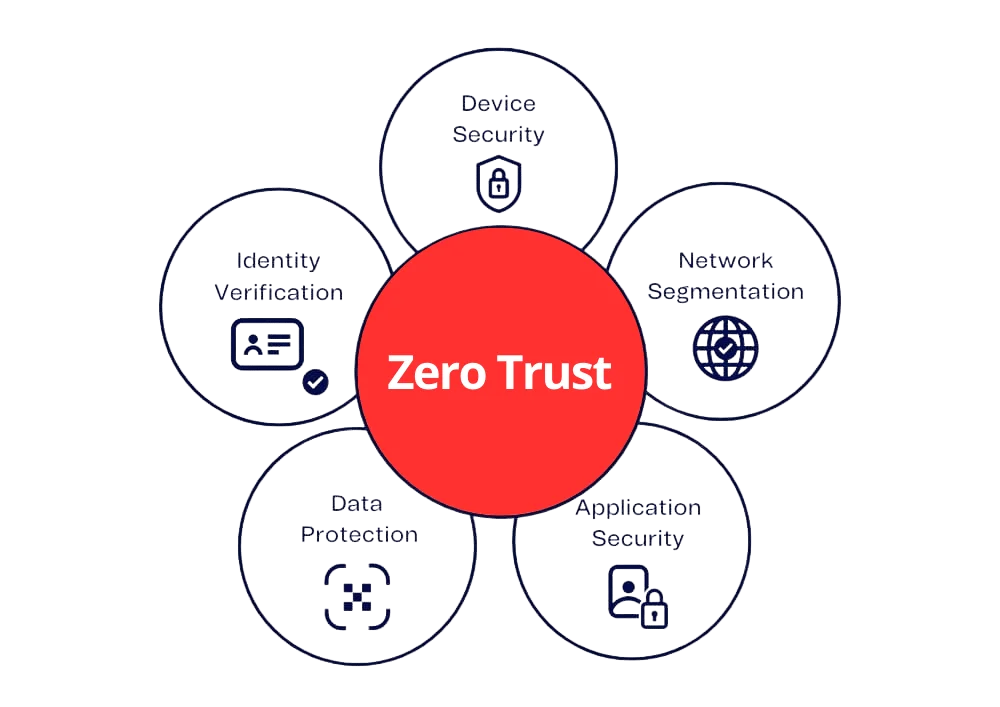
Zero Trust is implemented through a combination of technologies, processes, and policies designed to enforce strict access controls and continuously monitor suspicious behavior. Key components of a zero-trust architecture include:
- Identity and Access Management (IAM)
One of the cornerstones of Zero Trust is strong IAM, which involves verifying the identity of users, devices, and applications trying to access resources. Multi-factor authentication (MFA) is typically used to ensure access is granted only to legitimate users and devices. IAM also enforces the principle of least privilege by providing granular access control and ensuring users can only access the resources they need. - Network Segmentation and Micro-Segmentation
Network segmentation divides the network into smaller, isolated zones, and micro-segmentation takes this further by applying security policies on a per-application or per-user basis. This approach limits the scope of any potential breach and prevents attackers from moving freely within the network. Each segment can have security controls, such as firewalls, intrusion detection systems, and access policies. - Endpoint Security
In a zero-trust model, devices must meet specific security standards before accessing network resources. This means ensuring that devices are correctly configured, have up-to-date security patches, and are protected by antivirus or endpoint detection and response (EDR) software. Endpoint security prevents compromised devices from accessing sensitive data or systems. - Data Encryption
Zero Trust often involves encrypting data at rest and in transit to ensure that sensitive information remains secure even if malicious actors intercept it. Encryption, along with strong access controls, helps protect the confidentiality and integrity of data throughout its lifecycle. - Behavioral Analytics and Continuous Monitoring
Continuous monitoring plays a key role in Zero Trust by detecting anomalous behavior that might indicate a breach or suspicious activity. Behavioral analytics tools analyze user and device behavior over time, establishing a baseline of regular activity. Any deviation from this baseline can trigger alerts and automatic security responses, such as restricting access or requiring re-authentication.
Benefits of Adopting Zero Trust
Benefits of using Zero Trust for cyber security that you can use in your company:
- Improved Security and Reduced Risk of Data Breaches
Zero Trust significantly improves an organization’s security posture by reducing the attack surface and limiting access to sensitive data. Even if an attacker gains access to one part of the network, they face multiple layers of defense and cannot move freely across the network. The continuous monitoring of user and device behavior also helps detect and mitigate attacks before they cause significant damage. - Protection Against Insider Threats
Traditional security models often assume that internal users can be trusted, but Zero Trust treats all internal or external users equally. This approach helps protect against insider threats, where malicious or compromised users within the organization could otherwise gain unauthorized access to critical systems or data. - Better Control Over Access to Cloud Services
With the increasing adoption of cloud services, organizations need a way to manage access to cloud applications and data securely. Zero Trust provides a robust framework for managing access to cloud environments, ensuring that only authorized users and devices can access sensitive cloud resources. - Simplified Compliance Management
Many industries have strict regulatory requirements for protecting sensitive data. Zero Trust can help organizations meet these compliance standards by enforcing strict access controls, monitoring for unauthorized access, and ensuring that data is encrypted and securely stored. - Enhanced User Experience
While Zero Trust emphasizes security, it doesn’t compromise user experience. With the use of technologies like Single Sign-On (SSO) and MFA, users can enjoy secure, seamless access to the applications and resources they need without needing to authenticate or remember passwords.
Conclusion
Zero Trust is a revolutionary approach to cybersecurity that shifts the paradigm from perimeter-based security to a more rigorous, identity-centric model. Zero Trust minimizes the risk of data breaches, insider threats, and unauthorized access by assuming no trust, verifying identities, applying the least privileged access, and continuously monitoring user and device behavior.
While it presents challenges in terms of implementation and ongoing management, the benefits of adopting a Zero Trust architecture—such as improved security, better cloud protection, and simplified compliance—make it an essential strategy for modern organizations looking to safeguard their data and systems in a rapidly changing threat landscape.


