In today’s rapidly evolving digital landscape, cybersecurity has become a top priority for organizations of all sizes. With the increasing frequency and sophistication of cyberattacks, traditional security measures such as firewalls and antivirus software are no longer sufficient to protect against modern threats. One of the most effective solutions to combat these evolving cyber threats is Endpoint Detection and Response (EDR).
In this article, we will explore what EDR is, how it works, its key features, and the benefits of implementing EDR solutions in an organization’s cybersecurity strategy.
What is Endpoint Detection and Response (EDR)?
EDR is a cybersecurity technology designed to monitor and protect endpoints—such as computers, mobile devices, servers, and other networked devices—from potential security breaches. By continuously monitoring endpoint activity, EDR systems can detect suspicious behavior, respond to threats in real time, and provide valuable insights into security incidents.
Endpoint Detection and Response (EDR) refers to a category of security tools and practices focused on detecting, investigating, and responding to suspicious activities on endpoints in a network. Endpoints, any devices connected to a network (e.g., laptops, desktops, smartphones, servers, and IoT devices), are often targeted by cybercriminals due to their direct connection to sensitive data and business processes.
EDR solutions provide real-time monitoring, continuous data collection, threat detection, and automated responses to malicious activities on these endpoints. The ultimate goal of EDR is to reduce the attack surface, minimize the damage caused by security breaches, and enable faster response times to security incidents.
How Does EDR Work?
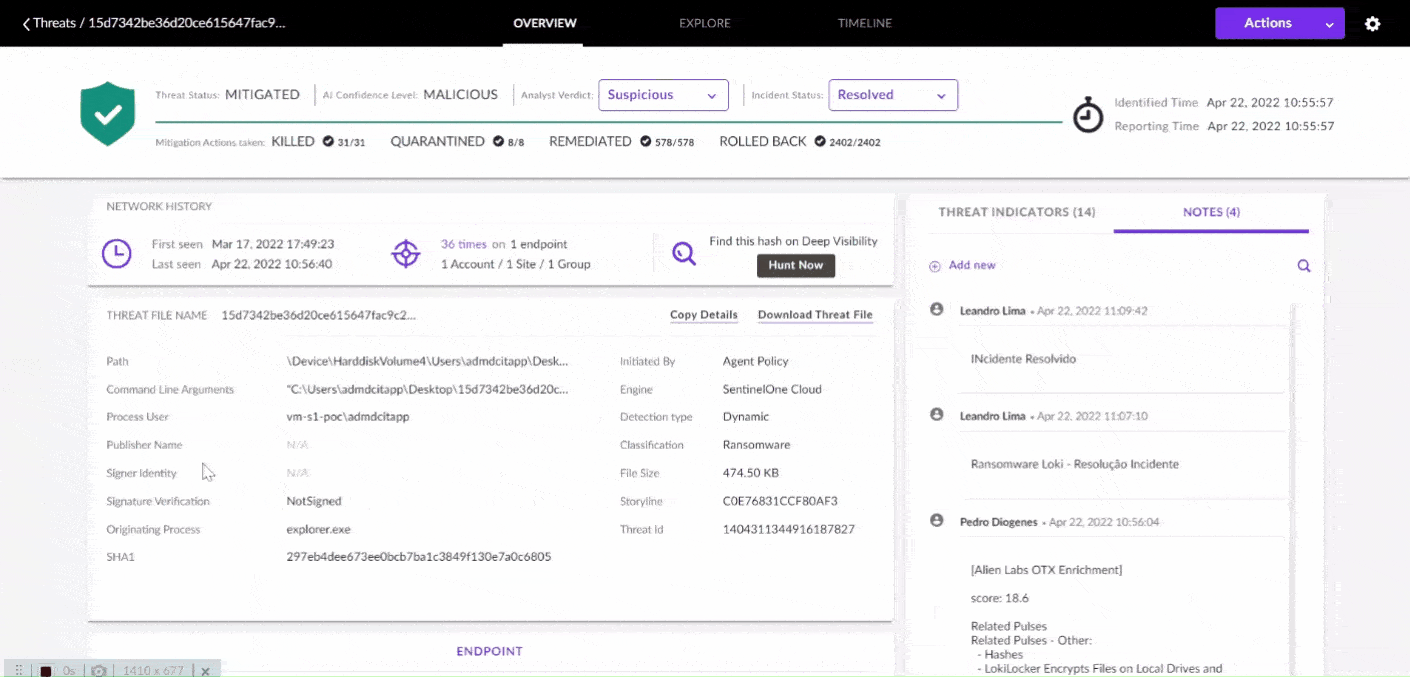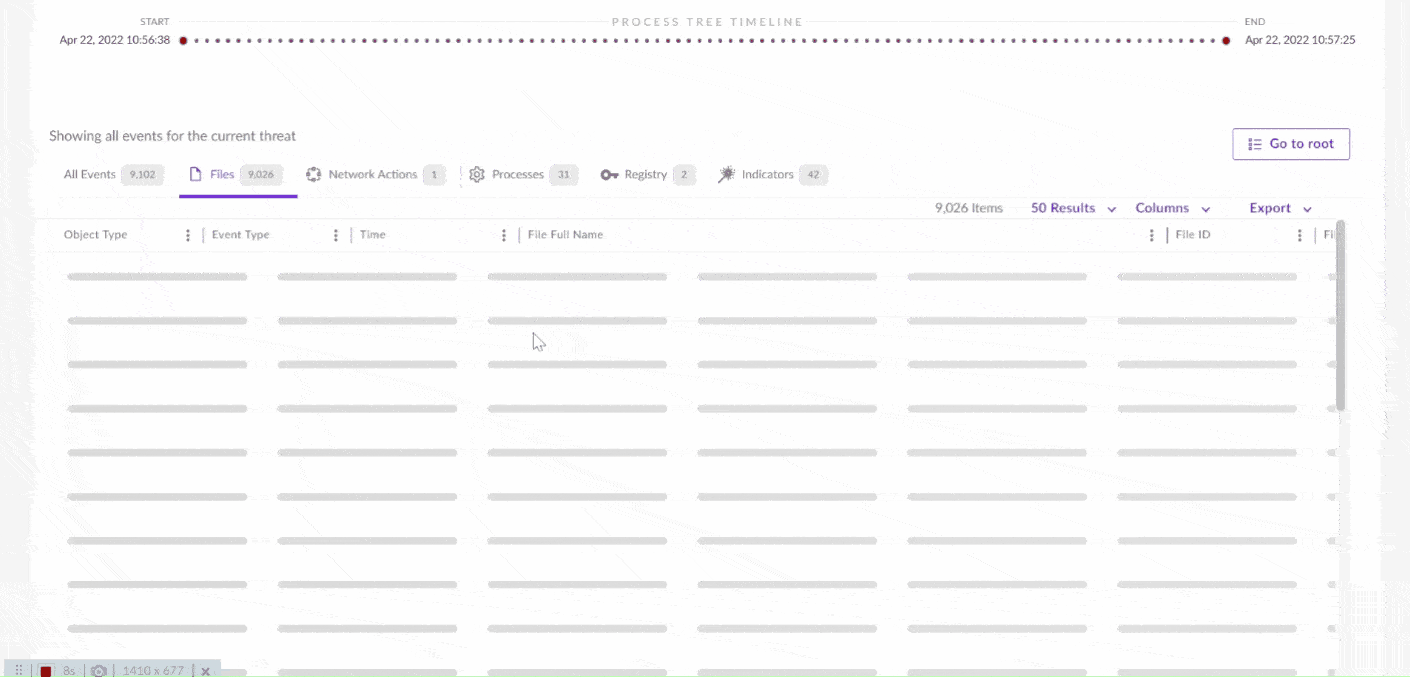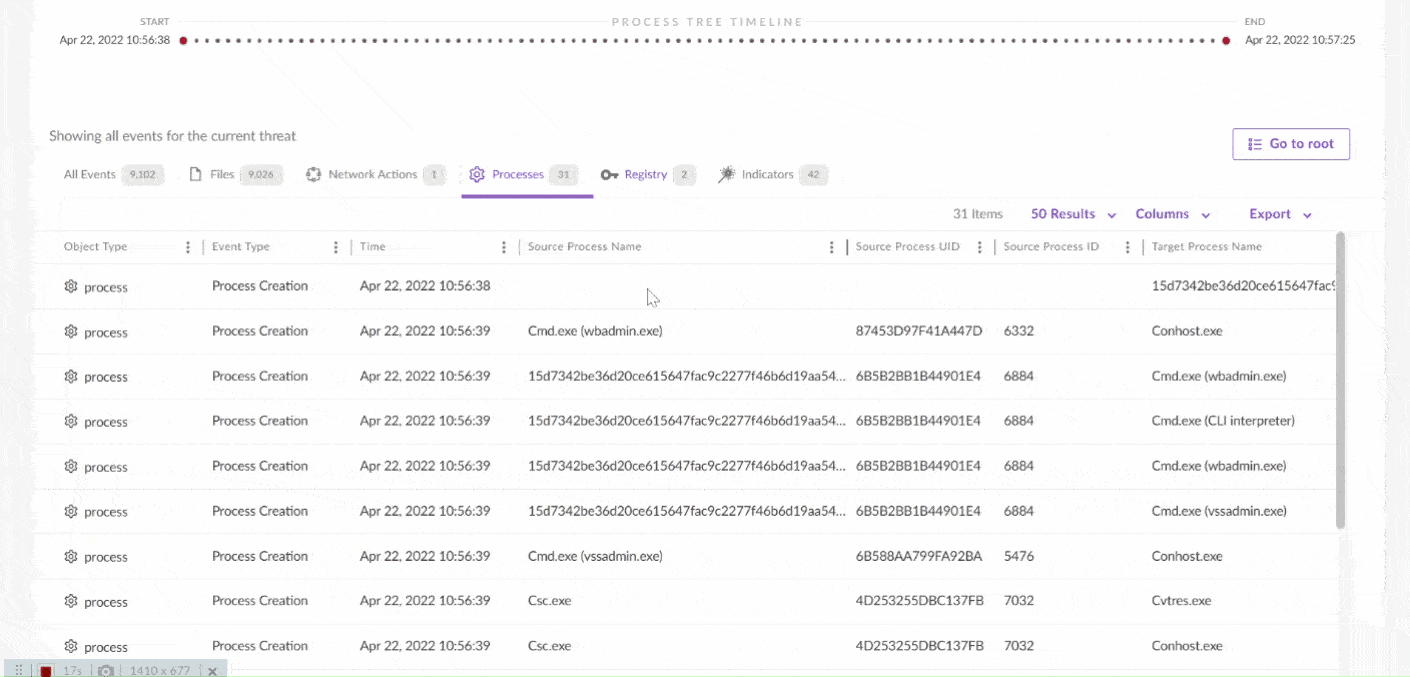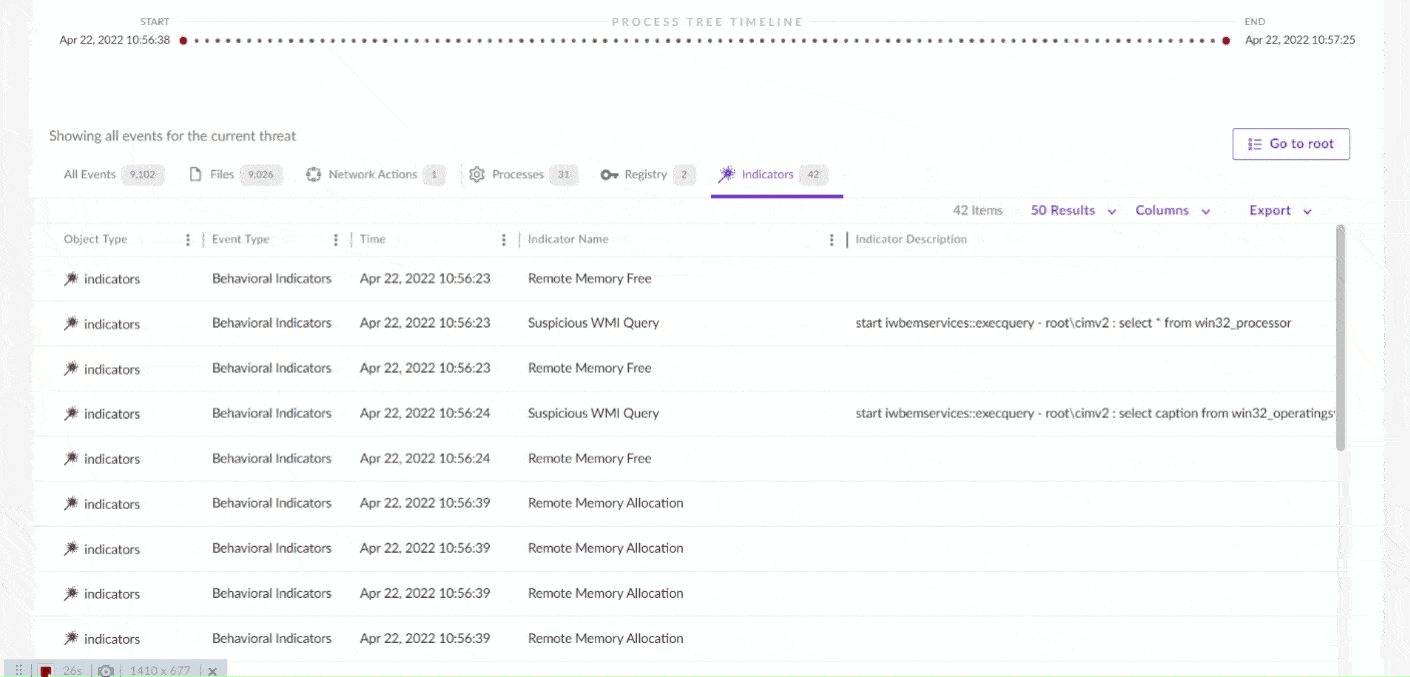
EDR solutions continuously monitor endpoints for any signs of malicious activity or unauthorized access. The system typically includes the following key components:
1.Data Collection
EDR systems collect and aggregate data from endpoints, such as system logs, process data, file integrity changes, network connections, and user activities. This data is used to create a baseline of normal endpoint behavior, which helps detect anomalies.
2.Threat Detection
EDR uses advanced detection techniques like machine learning, behavioral analysis, and signature-based methods to identify suspicious activities. The system looks for patterns or actions that deviate from the expected behavior of an endpoint. For example, it may flag an unusually high volume of file transfers, unauthorized access attempts, or abnormal network traffic.
3. Incident Response
Once a potential threat is detected, EDR systems can automatically take predefined actions to mitigate the risk. This may include isolating the affected endpoint, killing malicious processes, blocking malicious IP addresses, or quarantining suspicious files. Some EDR solutions provide security analysts with detailed information for manual investigation and response.
4. Forensic Analysis
EDR solutions provide tools for security teams to investigate and analyze security incidents. They collect data and create logs that can be used to trace the origin of the attack, identify affected systems, and understand how the attack progressed. This enables security teams to develop a more effective response and prevent future attacks.
5. Continuous Monitoring
EDR solutions continuously monitor the endpoints in real time, ensuring that no suspicious activities go unnoticed. The system also provides alerts when new threats are detected, allowing security teams to act quickly and reduce the time to contain an attack.
Key Features of EDR Solutions
There are 8 solutions offered by Endpoint SentinelOne (EDR), among them are:
- Real-Time Threat Detection: One of the core features of EDR solutions is their ability to detect threats in real time. By constantly monitoring endpoint activities and applying advanced algorithms to identify malicious behaviors, EDR systems can quickly identify and stop potential attacks before they can cause significant harm.
- Advanced Behavioral Analysis: EDR uses behavioral analytics to understand typical endpoint activity and to detect deviations from this behavior. This helps identify novel threats that might not have a known signature or that have been designed to evade traditional security measures.
- Automated Incident Response: EDR solutions can automatically take predefined actions when a threat is detected, such as isolating the affected device or blocking malicious network traffic. This reduces the time it takes to respond to an attack and limits the potential damage.
- Root Cause Analysis: EDR systems offer tools for investigating and identifying the root cause of an attack. By analyzing endpoint activity, security teams can determine how the threat entered the network, what systems were affected, and how the attack unfolded.
- Threat Hunting: EDR solutions provide security teams with tools to search for potential threats within the network proactively. This process, known as threat hunting, involves searching for signs of suspicious activities and vulnerabilities before attackers can exploit them.
- Integration with Other Security Tools: EDR solutions are often integrated with security tools, such as Security Information and Event Management (SIEM) systems, firewalls, and intrusion detection systems (IDS). This integration allows for a more comprehensive and coordinated response to threats across the network.
- Cloud Integration: Many EDR solutions offer cloud integration, enabling them to monitor endpoints across locations and protect remote devices. This is especially important in today’s hybrid work environment, where employees may work from multiple locations and use various devices.
Benefits of EDR Solutions for Your Company
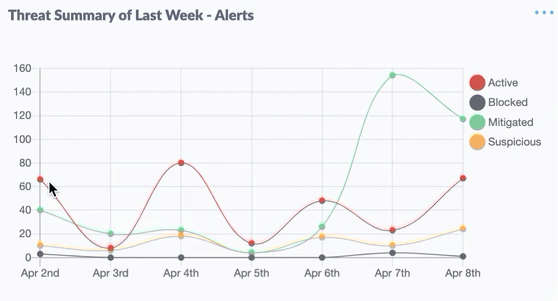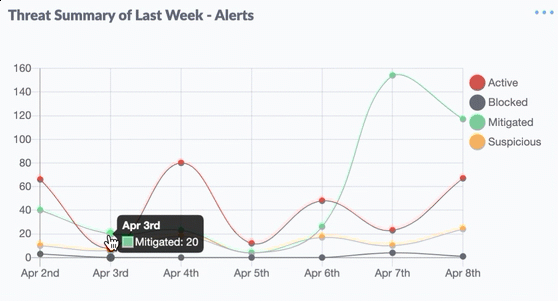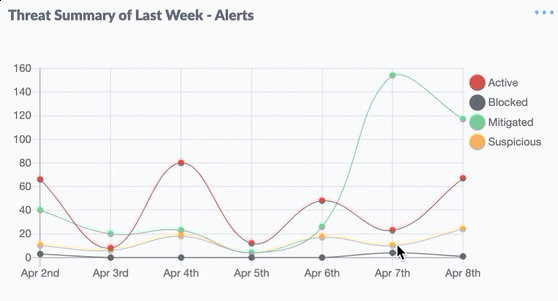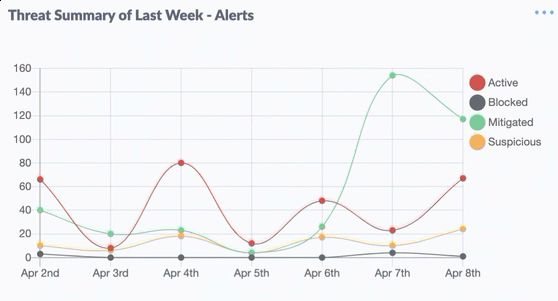
Above, we have discussed the Main Features of EDR Solutions, now the benefits you will get if you use Endpoint (EDR) from SentinelOne, there are:
1.Enhanced Threat Detection and Prevention
EDR solutions provide superior threat detection capabilities compared to traditional security tools. By continuously monitoring endpoint activity, EDR can detect and respond to threats in real time, minimizing the chances of a successful attack. Combining behavioral analysis, machine learning, and signature-based detection ensures that even advanced, unknown threats can be identified and mitigated.
2.Faster Incident Response
The automated response capabilities of EDR systems help contain threats faster and limit their spread. By isolating affected endpoints and blocking malicious activity immediately, EDR reduces the time between detection and remediation, preventing further damage.
3. Comprehensive Visibility into Endpoint Activity
EDR solutions provide detailed visibility into endpoint activity, enabling security teams to monitor system behavior and track all actions taken by users and processes. This data can be invaluable when investigating incidents and determining the extent of an attack.
4.Reduced Attack Surface
By continuously monitoring endpoints and automatically responding to suspicious activities, EDR systems help reduce the attack surface. This proactive approach limits the opportunities for attackers to exploit vulnerabilities and gain unauthorized access to critical systems.
5.Improved Compliance
EDR solutions help organizations meet compliance requirements by ensuring that endpoints are secure and sensitive data is protected. With the ability to monitor and track activities across endpoints, organizations can demonstrate their commitment to meeting industry standards and regulations, such as GDPR, HIPAA, and PCI-DSS.
6.Scalability for Growing Networks
As businesses grow and expand, the number of endpoints they must protect also increases. EDR solutions are highly scalable, making it easier for organizations to secure their expanding network of devices and maintain consistent protection across multiple locations.
7.Better Forensic Investigation
In the event of a security breach, EDR provides valuable forensic data that can be used to understand how the attack occurred and what actions the attackers took. This helps organizations learn from the incident and strengthen their defenses against future threats.
Conclusion
Endpoint Detection and Response (EDR) is essential to modern cybersecurity strategies, providing comprehensive protection for endpoints against various cyber threats. With real-time monitoring, advanced threat detection, and automated response capabilities, EDR enhances an organization’s ability to detect, respond to, and prevent attacks before they cause significant harm.
As businesses embrace digital transformation and remote work, investing in a robust EDR solution is critical to maintaining a secure network environment and protecting sensitive data from emerging threats.