Cyber threats continue to evolve rapidly in an increasingly digital and connected world. Organizations worldwide face significant challenges in managing the security risks associated with increasingly sophisticated and diverse cyberattacks.
Many companies are now turning to more advanced and integrated security solutions to protect valuable assets and data. One such technology gaining popularity is XDR (Extended Detection and Response), with SentinelOne being one of the leaders in providing XDR platforms.
This article will delve deeply into XDR and how it works.
What is XDR?
XDR (Extended Detection and Response) is a security approach that integrates various data sources and technologies to provide more holistic protection against cyber threats. Compared to traditional security solutions that tend to be fragmented, XDR aims to unify different layers of defence and offer a comprehensive view of potential threats.
XDR combines data from endpoints, networks, servers, emails, and the cloud to detect and respond to threats more effectively and efficiently.
How XDR (Extended Detection and Response) Works
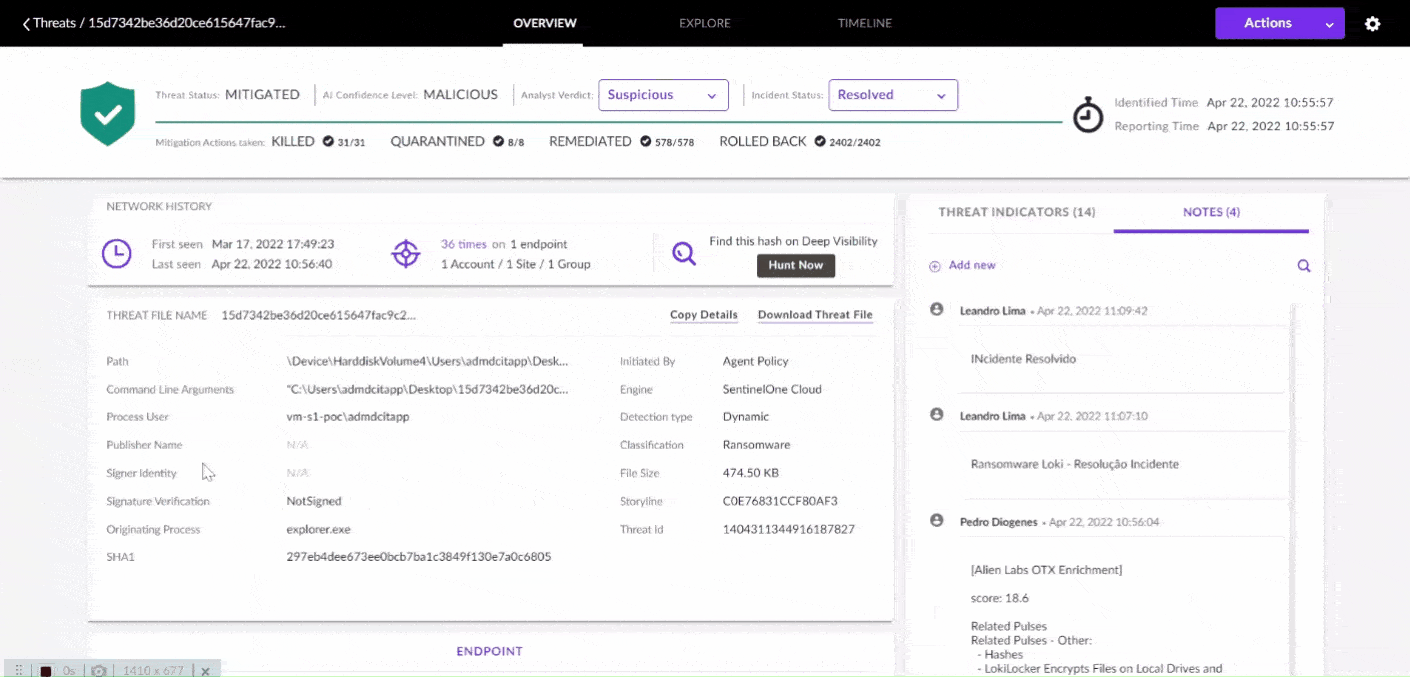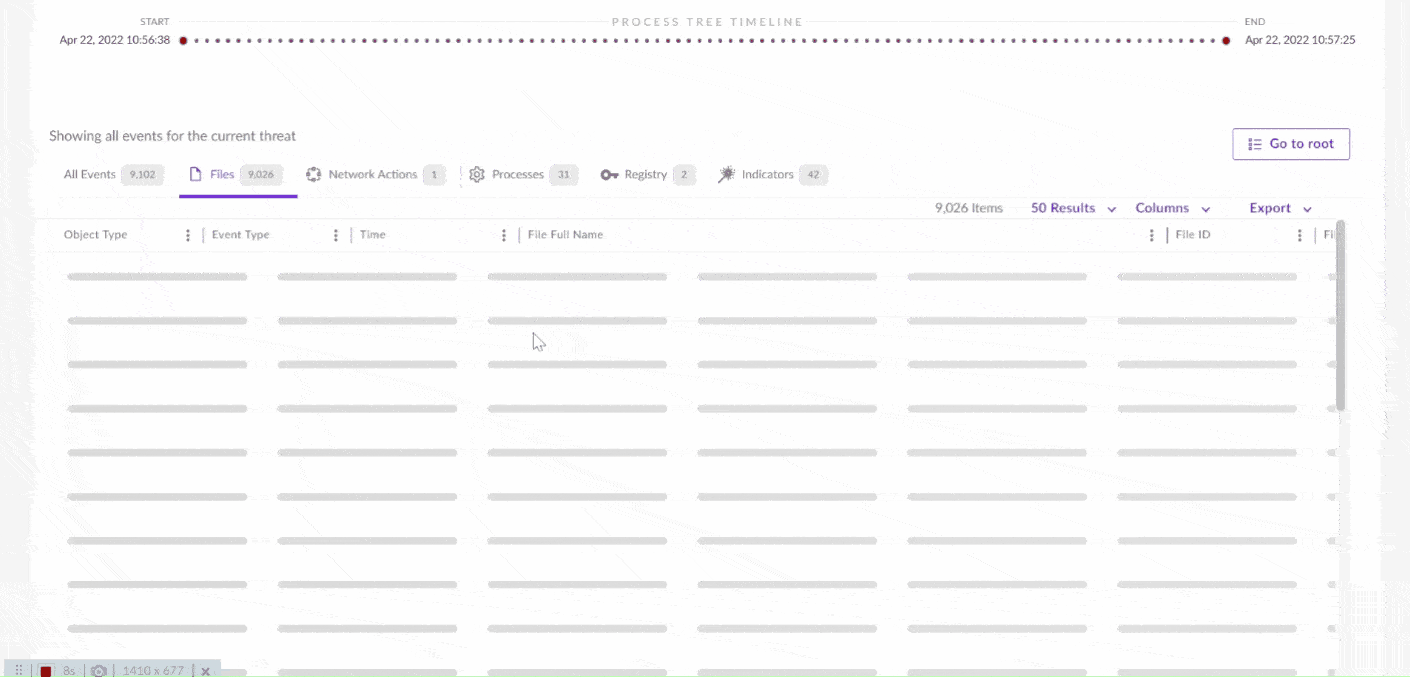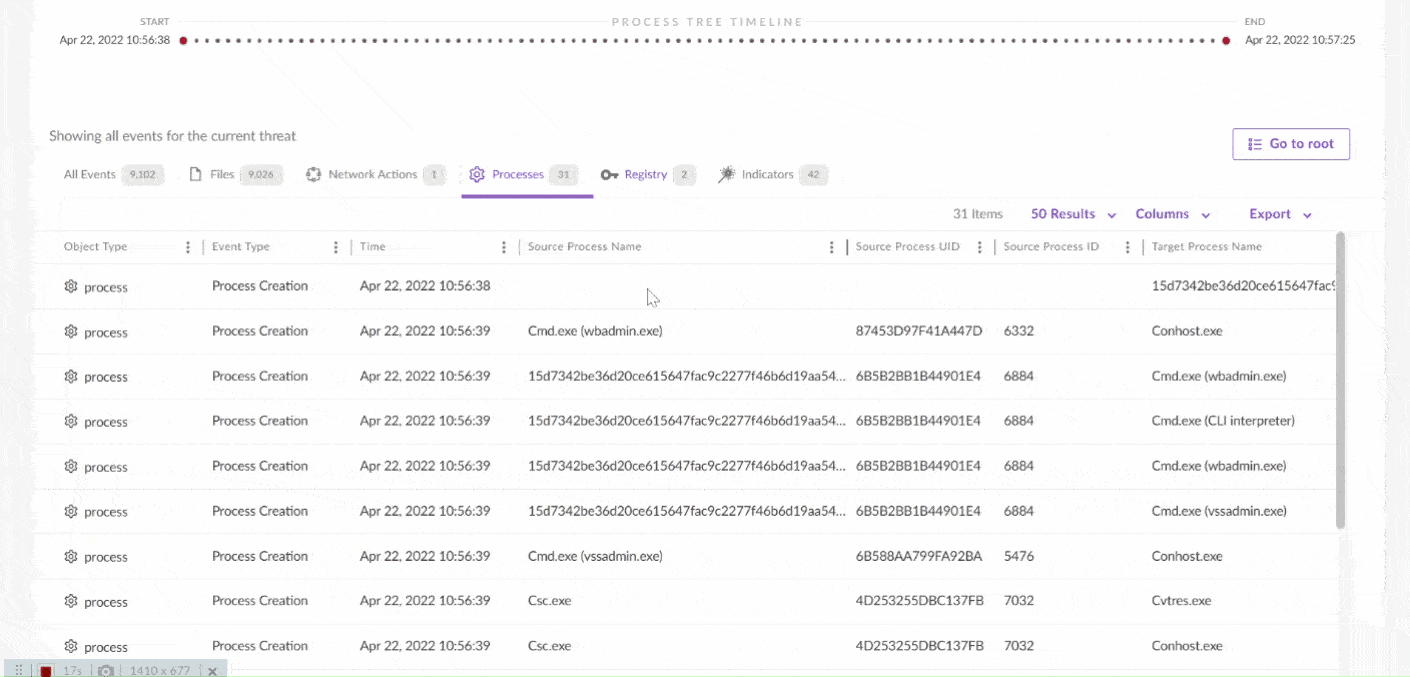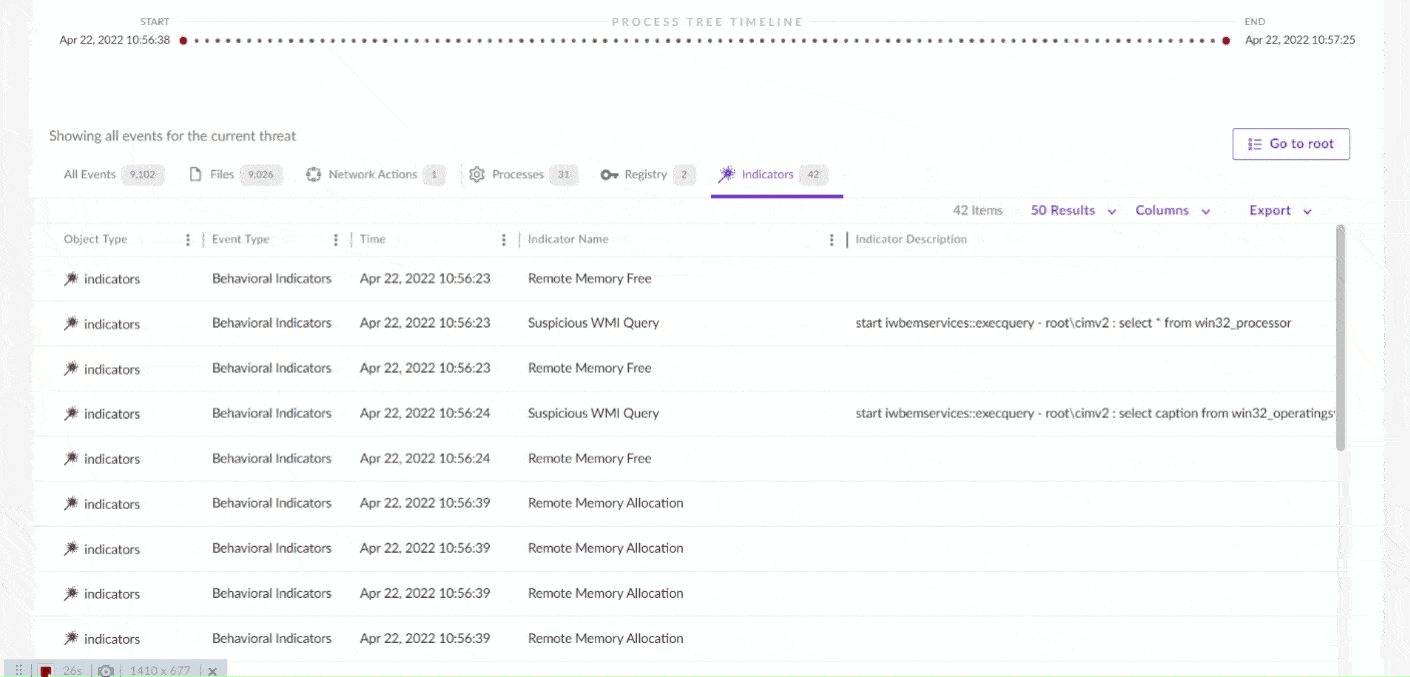
XDR (Extended Detection and Response) works by integrating and connecting various security systems (such as EDR, NDR, firewalls, SIEM, etc.) into a centralized platform that is always up-to-date. This allows organizations to detect, analyze, and respond to threats more quickly, thoroughly, and efficiently. Below are the steps on how XDR works:
- Data Collection from Various Sources XDR begins by collecting data from various points across the IT infrastructure. This includes endpoints (user devices such as laptops, desktops, and mobile devices), networks (traffic passing through firewalls, network devices, and servers), and applications and cloud systems. Some familiar data sources collected include:
- Endpoint: Data from user devices (such as computers and mobile devices) containing information about user activity, software being run, and processes in progress.
- Network: Network traffic and data flow across network devices, such as firewalls, routers, and switches.
- Servers and Cloud: Data from servers (on-premise and in the cloud), applications running, and interactions between applications.
- Other Security System Logs: Data from other security tools like SIEM (Security Information and Event Management), IDS/IPS (Intrusion Detection/Prevention Systems), and NDR (Network Detection and Response).
- Collecting this data is to get a comprehensive view of all activities and movements within the system so that any threats or suspicious patterns can be detected.
- Correlation and Data Analysis After collecting data, XDR analyzes and correlates data from these different sources. This is one of the main strengths of XDR, as it doesn’t just look at data in isolation (e.g., from endpoints or networks) but combines information to get a holistic view of potential threats.
- Event Correlation: XDR links and matches events or activities detected across various layers to look for patterns indicating a threat. For example, suppose there is an anomaly on an endpoint (such as suspicious device behaviour). In that case, XDR will check for similar patterns in the network or related applications, enabling the identification of broader attacks.
- Machine Learning and AI: XDR often uses artificial intelligence (AI) and machine learning (ML) algorithms to analyze data more deeply and identify unusual patterns or anomalies that static rules may not detect. AI and ML help identify new threats that were previously unrecognized.
- Behavioural Analysis: XDR can monitor system and user behaviours to see if any activity deviates from the normal. For example, a sudden spike in data requests or unusual logins on an endpoint or application could indicate communication between infected devices or behaviour suggesting an attack.
- Threat Detection With the analysis and correlation done, XDR can detect threats more effectively, including more sophisticated attacks that may be difficult for traditional solutions to identify.
- Malware and Ransomware Detection: XDR can detect devices infected with malware or ransomware by analyzing suspicious file or process behaviours.
- Lateral Attacks: One of XDR’s main capabilities is detecting lateral attacks, which occur when an attacker gains access to one device or point within the network and attempts to move further into the IT infrastructure. XDR can observe and identify this movement between various points and prevent further spread.
- Coordinated Attacks: XDR can also detect attacks involving multiple stages or layers, such as APT (Advanced Persistent Threats), which may start at an endpoint, move to servers, and eventually attack data in the cloud.
- Response to Threats Once a threat is detected, XDR responds with either automatic or manual actions to mitigate or stop the impact of the attack. This response can include:
- Automated Response: XDR can automatically respond to threats based on predefined rules. For example, suppose XDR detects malware on an endpoint. In that case, the system can automatically isolate the infected device to prevent further spread.
- Notifications and Escalation: If XDR detects a more complex or dangerous threat, the system will send messages to the security team with complete details about the detected threat and necessary actions. These notifications may include threat IDs, affected devices, and signs of suspicious behaviour.
- Process Termination and Access Blocking: XDR can terminate suspicious processes on an endpoint or block suspicious communications on the network to stop the attack before it achieves its goal.
- Endpoint Isolation: To prevent further spread, XDR can isolate the infected device from the network or disable access to specific applications or data.
- Advanced Controls: If the attack continues or is highly sophisticated, XDR can direct the security team to take further actions, including more profound analysis and system repairs.
- Recovery and Forensic Analysis After the threat is addressed, XDR supports recovery and forensic analysis processes to understand what happened, how the attack occurred, and what can be done to prevent similar attacks in the future.
- System Recovery: The security team can restore affected systems and data, such as recovering infected files or fixing vulnerabilities that attackers use to access the network.
- Forensic Analysis: XDR provides tools and reports to analyze the attack in-depth. This includes looking at attack patterns, involved devices, and the pathways the attackers use to help prevent future incidents.
- Learning from Incidents: XDR allows organizations to take preventive actions to strengthen their security policies based on lessons learned from the incidents. This includes updating detection rules, enhancing access controls, and raising security awareness.
Conclusion
XDR (Extended Detection and Response) integrates various security layers to provide greater visibility, detect threats more sophisticatedly, and respond more quickly to incidents. By collecting data from multiple sources (endpoints, networks, applications, servers, and the cloud), XDR provides a more comprehensive view of the threats occurring across the entire IT infrastructure.
Through data correlation, behaviour-based detection, and automated responses, XDR can identify and address threats more efficiently, providing faster responses and reducing potential attack damage.
Investing in SentinelOne is a strategic step to enhance network protection and ensure business continuity.
Do you want to discuss the detailed use of SentinelOne in your company or organization with Leyun Asia as the Official SentinelOne Partner in Indonesia? Contact us using the form below.