In an increasingly digital era, websites and online applications have become crucial for business needs, government, and personal communication. However, behind this technology’s conveniences are lurking threats, one of which is the Distributed Denial of Service (DDoS) attack.
A DDoS attack is a type of cyber attack aimed at making services or websites inaccessible by overwhelming servers or networks with massive amounts of data traffic.
In this article, we will delve deeply into what a DDoS attack is, how it works, and the steps that can be taken to protect oneself from this threat.
Understanding DDoS Attacks
A Distributed Denial of Service (DDoS) attack is an attempt to stop or disrupt legitimate users’ access to services or systems by sending overwhelming requests until the server cannot handle them. When this attack is conducted in a distributed manner involving many computers or devices spread across various locations, it is referred to as a Distributed Denial of Service (DDoS) attack.
The main goal of a DDoS attack is to overload a server or service’s resources so that it cannot serve requests from legitimate users, ultimately causing the service to become unavailable or slow.
How DDoS Attacks Work
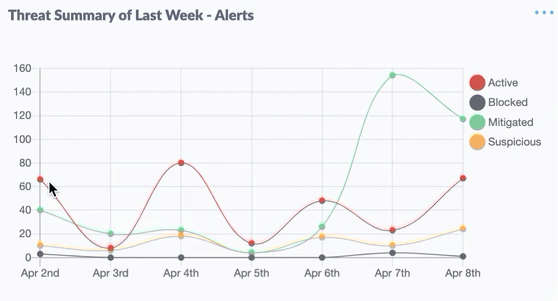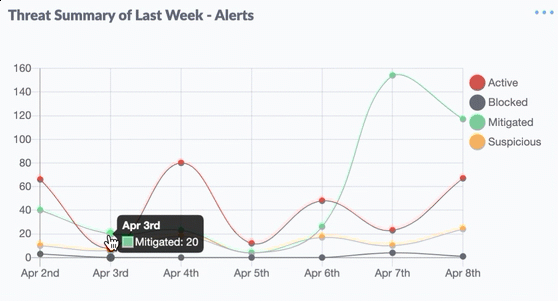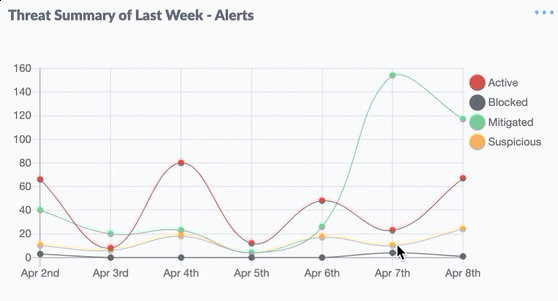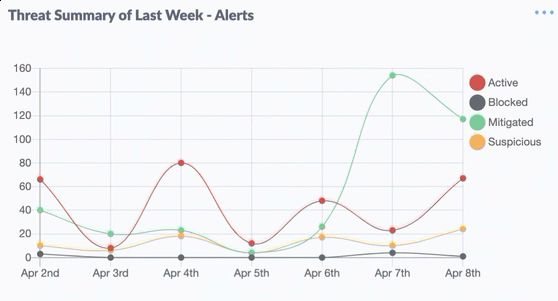
DDoS attacks operate by utilizing a botnet, which is a network of devices infected with malware and controlled by the attacker without the knowledge of the device owners. Here’s a detailed explanation of how DDoS attacks are typically executed:
- Infection and Control of Devices: The attacker first spreads malware that can infect computers, routers, or IoT (Internet of Things) devices. These devices, known as “zombies” or bots, are then controlled by the attacker through a command and control (C&C) server.
- Launching the Attack: Once the botnet is formed, the attacker can send commands to direct all infected devices to send requests simultaneously to the targeted server or website. These requests can be HTTP, TCP, UDP, or other types of data packets that can overload the server.
- Flooding: The primary process in a DDoS attack is flooding, which involves inundating the target server or network with a very high traffic volume. Servers or networks that cannot handle incoming traffic will become slow or inaccessible.
- Increasing Impact: In some cases, attackers may sustain DDoS attacks to ensure that the service remains unavailable for an extended period. Typically, the attacker will combine several types of attacks, such as UDP flood, TCP SYN flood, or HTTP flood, to maximize the impact.
Types of DDoS Attacks
DDoS attacks can be categorized based on how they operate and the type of traffic they send to the target. Here are some common types of DDoS attacks:
- Volume-based attacks aim to flood the network or server with massive traffic. They are often executed by sending many data packets, such as UDP or ICMP floods.
- Protocol attacks: These attacks exploit vulnerabilities in network protocols to disrupt the performance of servers or network devices. An example is a SYN flood, where the attacker sends incomplete connection requests to exhaust server resources.
- Application layer attacks target the application layer, aiming to consume the resources used to run web applications. An example is an HTTP flood, which utilizes repeated HTTP requests to keep the web server busy and unable to respond to legitimate requests.
- Hybrid attacks combine several attack techniques, such as merging TCP SYN floods with HTTP floods, to worsen the impact and make it harder to stop.
Impact of DDoS Attacks
DDoS attacks can negatively impact companies, individual users, and internet service providers. Some of the main impacts of DDoS attacks include:
- Service Disruption: Services or websites targeted by attacks will experience disruptions that can lead to downtime. This can harm businesses, especially those reliant on the availability of their services for operations.
- Financial Loss: Besides the costs for service recovery, companies that fall victim to DDoS attacks may also lose revenue because customers cannot access their websites or applications.
- Reputational Damage: Failure to protect a website or service from DDoS attacks can damage a company’s reputation, especially if customers feel that their services are unreliable.
- Increased Load on Network Infrastructure: DDoS attacks can strain network infrastructure, raising maintenance costs and slowing system performance.
Read more : 8 Ways to Overcome DDoS Attack Using Cloudflare
How to Protect Against DDoS Attacks
Protecting systems and services from DDoS attacks requires a comprehensive approach and involves various techniques. Here are some steps that can be taken to protect systems from DDoS threats:
- Regular Traffic Monitoring: Actively monitoring network traffic can help detect DDoS attacks early. Network monitoring tools can help identify unusual traffic spikes so that preventive measures can be taken promptly.
- Increasing Infrastructure Capacity: One way to mitigate the impact of DDoS attacks is to enhance server and network capacity. This includes using high-capacity servers and load-balancing systems that evenly distribute traffic loads.
- Using DDoS Protection Services: Some security service providers, like Cloudflare or AWS Shield, offer DDoS mitigation services that can help protect websites and applications from DDoS attacks by filtering and managing harmful traffic.
- Firewalls and Intrusion Prevention Systems: Properly configured firewalls and intrusion prevention systems can help identify and block DDoS attacks at an early stage.
- Using SCDN (Secure Content Delivery Network): This service from Edgeone Tencent Cloud can distribute traffic loads to servers located in various geographic locations, thereby reducing the impact of DDoS attacks.
- Protection Against Botnets: Keeping devices and servers connected to the internet secure from malware infections is crucial in preventing botnets from being used in DDoS attacks.
Conclusion
DDoS attacks pose a serious threat to network security and information systems. With a good understanding of how these attacks work and appropriate mitigation measures, we can reduce the risks and impacts of such attacks.
Investing in Anti-DDoS security is a strategic step to enhance network protection and maintain business continuity. If you want to discuss the details of using anti-DDoS solutions for your company or organization with Leyun Cloud Asia, please contact us using the form below.