DDoS (Distributed Denial of Service) attacks are among the most common and damaging forms of cyberattacks. These attacks make a website or online service inaccessible by overwhelming the server with massive fake traffic. As a result, the server becomes overwhelmed and unable to handle legitimate user requests. DDoS attacks can lead to website downtime, business losses, and significant service disruptions.
However, you can safeguard your website or application from DDoS attacks by using protection services like Cloudflare. In this article, we’ll discuss what a DDoS attack is, how it works, and how Cloudflare can be an effective solution to combat such attacks.
What is a DDoS Attack?
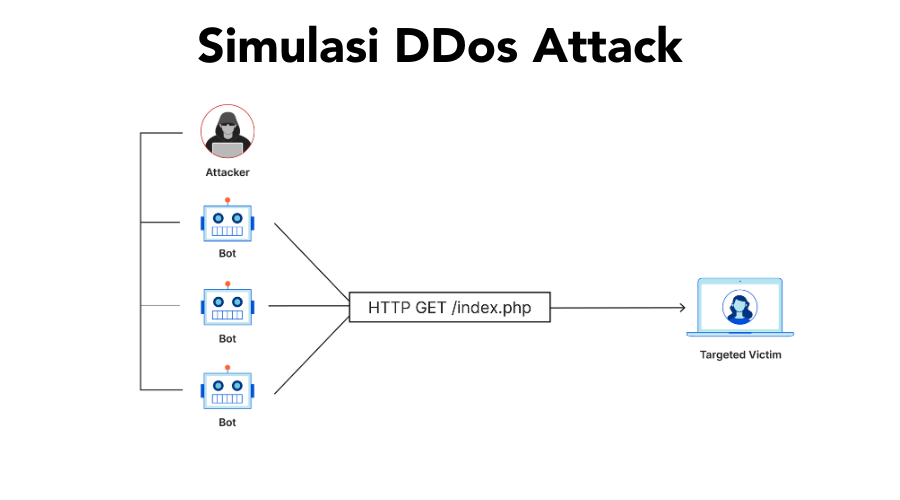
A DDoS attack involves numerous devices infected with malware (known as a botnet) controlled by an attacker. These devices are then used to make requests to the target website simultaneously, generating an overwhelming load on the accessed server. This causes:
– Server overload: The server cannot handle many requests and eventually slows down or crashes.
– Legitimate users cannot access the site: When an attack occurs, genuine users cannot access the website or service because the attack traffic consumes all the bandwidth and server resources.
There are several types of DDoS attacks, including:
– Volumetric Attacks: These overwhelm the network or server with large amounts of data to exhaust bandwidth.
– Protocol Attacks: These exploit weaknesses in network communication protocols, such as TCP/IP, to prevent the server from handling requests.
– Application Attacks: These target a website’s application layer, such as login pages or APIs, to flood the server with fake requests.
How Does Cloudflare Combat DDoS Attacks?

Cloudflare is one of the world’s leading services that provide protection against DDoS attacks. With a global network spread across more than 200 cities, Cloudflare can withstand large-scale DDoS attacks and keep websites online.
Here are 8 ways Cloudflare can help you face DDoS attacks:
1. Global Content Delivery Network (CDN)
Cloudflare’s global server network distributes your site’s content across multiple locations. This not only speeds up users’ access but also helps mitigate DDoS attacks.
How does this help against DDoS?
– During a DDoS attack, Cloudflare can distribute the excess traffic across all its servers, so the load isn’t handled by just one server.
– Cloudflare can also block traffic from botnets within its network before it reaches your server, reducing the attack’s impact.
2. Cloudflare DDoS Protection: Automatic Detection and Mitigation
Cloudflare has an automatic detection and mitigation system that monitors incoming traffic to your site in real time. If Cloudflare detects suspicious traffic patterns that may indicate a DDoS attack, the system immediately takes action to stop the attack.
Key Features:
– Always-On Protection: Cloudflare’s DDoS protection is always active without requiring additional configuration. This ensures that your site is always ready to face attacks at any time.
– Real-Time Attack Monitoring: Cloudflare monitors all traffic to your site and can block an attack within seconds.
– Layer 3, 4, and 7 Protection: Cloudflare protects against all types of DDoS attacks targeting network layers (layer 3 and 4) and application layers (layer 7), such as HTTP flood or volumetric attacks.
3. “I’m Under Attack” Mode
Cloudflare offers an “I’m Under Attack” mode, which can be activated when your site is experiencing a DDoS attack.
How does it work?
– When activated, this mode displays an interstitial page asking visitors to verify that they are human by solving a challenge (usually a CAPTCHA) before accessing the site.
– This ensures that bots cannot access your site, while legitimate users can enter after verification.
How to Activate:
– Log in to the Cloudflare dashboard.
– Select the site you want to protect.
– In the “Overview” tab, activate the “I’m Under Attack” mode.
4. Rate Limiting
Rate Limiting is a Cloudflare feature that helps control the number of requests an IP can make to your site within a specific time frame. This is especially useful for protecting against application-layer DDoS attacks like HTTP floods.
How does Rate Limiting help?
– Cloudflare will limit the requests from a single IP when it detects a suspicious traffic spike.
– This feature ensures that DDoS attacks using repeated HTTP requests won’t overload your server.
How to Activate Rate Limiting:
– Log in to the Cloudflare dashboard.
– Select your site.
– Go to the “Firewall” tab and choose Rate Limiting to set rules that limit requests from suspicious IPs.
5. Web Application Firewall (WAF)
Cloudflare also provides a Web Application Firewall (WAF) that protects your site from attacks on the application layer. WAF helps block malicious traffic targeting web application vulnerabilities like SQL injection, cross-site scripting (XSS), and more.
How does WAF protect against DDoS?
– The WAF has built-in security rules to recognize and block application-layer DDoS attacks.
– You can customize these rules to block traffic from specific IPs, countries, or suspicious traffic patterns.
6. Attack Analytics and Reporting
Cloudflare provides analytics tools that give you full visibility into all traffic coming to your site. These tools allow you to analyze attack patterns, identify suspicious IPs, and get detailed reports on blocked malicious traffic.
Advantages:
– Understand attack patterns and predict potential future threats.
– Assess the effectiveness of Cloudflare’s DDoS protection against ongoing attacks.
7. Zero Trust
Zero Trust is a security approach that does not automatically trust any network or user, whether internal or external.
Cloudflare integrates the Zero Trust principle with DDoS protection to provide maximum security. Here are some Cloudflare features supporting Zero Trust implementation:
How it works:
– Every time there is an access request to an application or system, Cloudflare Access verifies user credentials using Single Sign-On (SSO) integrated with identity providers (e.g., Google, Microsoft).
– Only users with permissions based on security policies can access the application.
Advantages in DDoS Mitigation:
– Access is not allowed for untrusted devices, minimizing the chance of botnets accessing your application.
– Enhances security at the application layer with identity- and device-based validation.
8. Argo Tunnel
With Argo Tunnel, internal applications remain hidden from the public internet, reducing the risk of being targeted by DDoS attacks. Argo Tunnel creates a secure “tunnel” between internal servers and the Cloudflare network without exposing the server IP to the public.
Advantages:
– Internal applications can only be accessed by verified users through Cloudflare Access.
– Eliminates the need to open ports or use a VPN, providing a safer and simpler solution.
Read more : 12 Tips to Overcome Latency Using Cloudflare
Conclusion
Cloudflare offers a comprehensive solution to protect websites and applications from DDoS attacks through automatic detection, global network protection, and the “I’m Under Attack” mode. When combined with a Zero Trust approach, Cloudflare ensures that every access request is verified, minimizing internal and external threats.
With Partner Cloudflare, you get not only protection from DDoS attacks and a modern security approach through Zero Trust, providing layered protection for your applications and critical company data against various cyber threats.
Don’t wait for your website to suffer from a DDoS attack; now is the time to activate Cloudflare!